How to secure Grub in Centos/RHEL 5/6/7 & 7.2
How to secure Grub in Centos/RHEL 5/6/7 & 7.2
In this tutorial we will learn to secure Grub. GRUB or Grand Unified Bootloader, is the default boot-loader for most of the Linux distributions. It provides a user the choice to boot one of multiple operating systems installed on a computer or select a specific kernel configuration available on a particular operating system’s partitions.Why do we need to secure GRUB ?
When we have password protected our root or general user account, so why would we need to assign password to GRUB. We need to secure GRUB because any person with little knowledge of Linux can google “HOW TO RESET ROOT PASSWORD ” & can reset the root password, if there is no password for GRUB-menu. Hence, we must secure our GRUB-menu.
In Centos/RHEL, GRUB2 bootloader is used & the process to assign GRUB-password is different as in RHEL/Centos 6 which uses GRUB.
NOTE:- Before we start I must warn you that you must backup of the files before editing them, incase we run into some trouble.
Securing GRUB-menu in RHEL/Centos 7 & 7.1
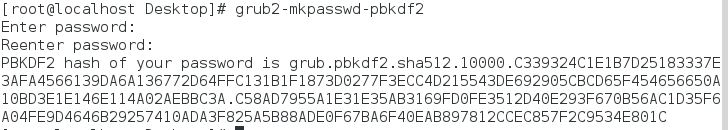
Firstly, we will generate an encrypted password by using the following command
grub2-mkpasswd-pbkdf2
You will be asked to enter a password twice. After you have entered the password, you will see password hash on your screen (see screenshot), copy the hash.
Next, open /etc/grub2/01_users & enter the following at the bottom of the file
set superusers=”john”
password_pbkdf2 john grub.pbkdf2.sha512.10000.19074739ED80F115963D984BDCB35AA671C24325755377C3E9B014D862DA6ACC77BC110EED41822800A87FD3700C037320E51E9326188D53247EC0722DDF15FC.C56EC0738911AD86CEA55546139FEBC366A393DF9785A8F44D3E51BF09DB980BAFEF85281CBBC56778D8B19DC94833EA8342F7D73E3A1AA30B205091F1015A85
password_pbkdf2 john grub.pbkdf2.sha512.10000.19074739ED80F115963D984BDCB35AA671C24325755377C3E9B014D862DA6ACC77BC110EED41822800A87FD3700C037320E51E9326188D53247EC0722DDF15FC.C56EC0738911AD86CEA55546139FEBC366A393DF9785A8F44D3E51BF09DB980BAFEF85281CBBC56778D8B19DC94833EA8342F7D73E3A1AA30B205091F1015A85
here, john is the user for the for GRUB-menu. You can modify & also use root or any other user here.
And we will now run following command to apply the grub changes
grub2-mkconfig –o /boot/grub/grub.conf
Now, reboot the system & press ’e’ to edit GRUB-parameters, you will now be asked for the credentials to access the menu.
Securing GRUB-menu in RHEL/Centos 7.2
Starting with RHEL 7.2, the above method for the securing Grub does not work. In RHEL 7.2 new utility ‘grub2-setpassword’ has been introduced. & procedure to set password is mentioned below.
Firstly run following command as “root” user
grub2-setpassword
then enter your password & confirm it. Hash for the password is created in /boot/grub/user.cfg & user i.e.”root” is defined in /boot/grub2/grub.cfg.
If you reboot system now & try to modify the boot entries, you will be asked to provide the credentials but you can boot the entries without credentials. In order to stop both unauthorized modification & unauthorized booting, we need to make changes to /boot/grub2/grub.cfg
Open the file & search for the boot entry you need to protect with password, it begins with menuentry. Once the entry is located, delete the –unrestricted parameter from it,
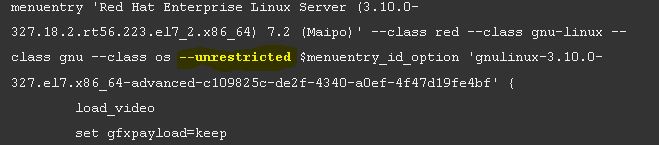
That’s it . Your GRUB-menu is now completely secured with a password.
Securing GRUB-menu in RHEL/Centos 5 & 6
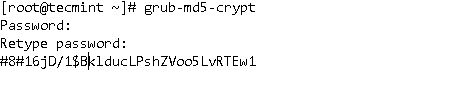
Using “root ” user enter the following command ,
grub-md5-crypt
then, enter the password, confirm it & copy the password hash created
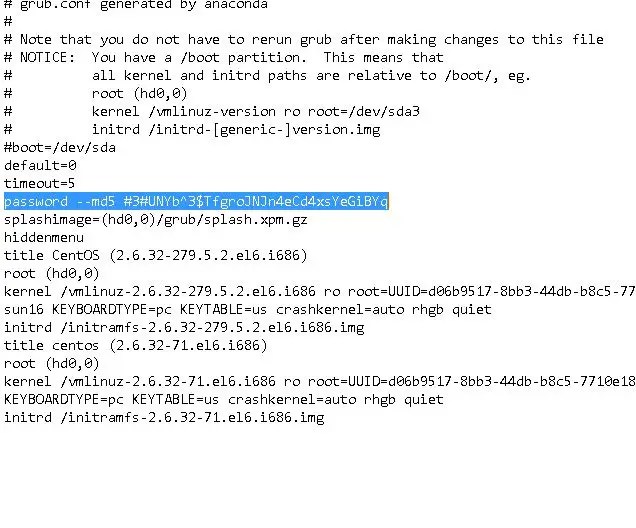
Next, open the file /boot/grub/grub.conf & copy the following line in it
password –md5 “password hash”
Lastly, restart your server & try to access you GRUB-menu, you will need to enter your credentials to access the menu.
This was our tutorial on how we can assign password to access GRUB-menu.
Comments
Post a Comment